Protect your business from cyber attacks
Penetration
Testing
Today, organisations are facing cyber-attacks of ever-increasing sophistication and intensity. Comprehensive penetration testing is an essential component to adequately defend against attacks from determined threat actors.
Application Security
Application security testing involves assessing the security of software applications to identify vulnerabilities that could be exploited by attackers.
Ensure the security of your mission-critical applications with Application Security Penetration Testing from SureCloud Cyber Services.
Our expert team can assess the security of applications, ranging from web to mobile apps, to the APIs that you rely on to connect sensitive data.
SureCloud Cyber Services delivers detailed reporting and debrief sessions to provide a clear roadmap for improvement.
Product Security Testing
Product security testing involves assessing the security of hardware and software products to ensure they are resistant to exploitation and unauthorised access.
Increasingly, threat actors are targeting connected hardware as a means of breaching an organization’s cyber defenses. Product Security from SureCloud provides a rigorous testing program, through which key connected and IoT device vulnerabilities are identified.
Our expert consultants will deliver reports and remediation, recommending the implementation of extensive rules and policies to govern the use of all devices tested by SureCloud.
Infrastructure Security
Infrastructure security testing focuses on evaluating the security of network infrastructure, including servers, routers, switches, and other components.
Your networks and devices are key targets for threat actors – does your organization possess the necessary skills and resources to secure them?
Objectively determine how easily your internal and external networks can be compromised with Infrastructure Security Penetration Testing from SureCloud Cyber Services.
Our expert team will identify your key areas of weakness and determine to what extent threat actors would be able to exploit your vulnerabilities to gain access.
Cloud Security
Cloud security testing focuses on evaluating the security of cloud-based services, including cloud platforms, applications, and data storage solutions.
With cloud adoption at an all-time high, ensuring the security of this virtual infrastructure has never been more important.
Our expert testing team will assess your cloud environments to ensure that best practice is being followed in your deployment of cloud and SaaS technologies.
SureCloud specialists will conduct in-depth configuration analyses of your cloud platforms to identify any errors which could be exploited by threat actors.
Identify and remediate key infrastructural weaknesses
Your networks and devices are key targets for threat actors – does your organization possess the necessary skills and resources to secure them?
Objectively determine how easily your internal and external networks can be compromised with Infrastructure Security Penetration Testing from SureCloud Cyber Services.
Our expert team will identify your key areas of weakness and determine to what extent threat actors would be able to exploit your vulnerabilities to gain access.

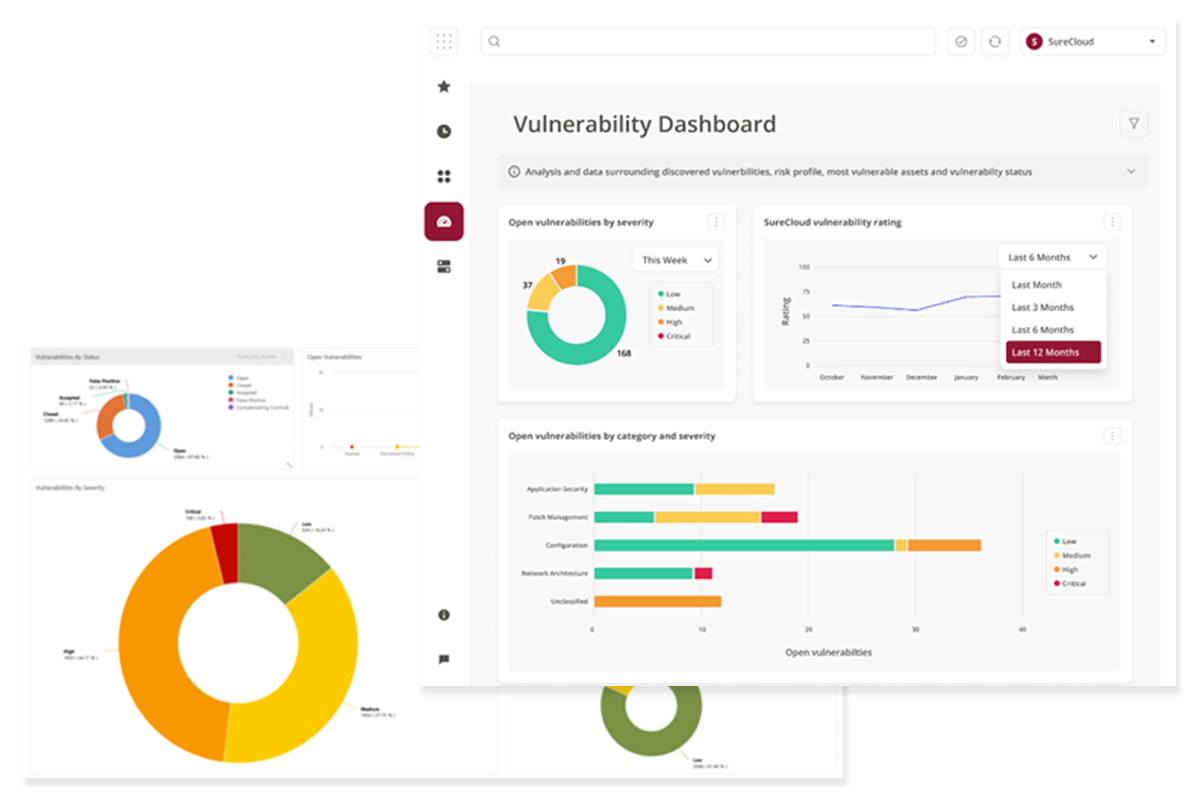
Vulnerability Management Platform
All our Penetration Testing results, recommendations and remediation support is provided via our Vulnerability Management Platform to make the identification, prioritisation and remediation of vulnerabilities quicker, more intuitive and visible in real time.
- Asset Management – classify your crown jewels with Impact Ratings to help prioritisation of remediation activities
- Vulnerability Management – categorisation, prioritisation risk scoring and remediation advice.
- Vulnerability Dashboard – centralized visibility of the vulnerability management process and health
- Remediation Activity Tracking – assign, track, set reminders and manage all remediation activity
- Dashboards and Reporting – comprehensive, real-time drill down dashboards and reports.

Why choose us?
We understand every organization possesses distinct security needs. Whether you require comprehensive application testing, long-term red team simulations, or in-depth analysis of legacy systems, we’re your dedicated partner in unearthing vulnerabilities before they become exploitable. Our comprehensive approach seamlessly integrates an advanced vulnerability management technology platform with the expertise of our highly accredited security
consultants.
By partnering with us, you gain:
- Deep expertise: Leveraging CREST and CHECK certified consultants with extensive industry experience.
- Comprehensive coverage: Combining automated scans with meticulous manual testing for exhaustive vulnerability identification.
- Customized penetration testing plans: Tailored to your unique requirements and risk profile.
- Proactive protection: Uncovering vulnerabilities before adversaries, empowering you to address them effectively.
Accreditations & Certifications







Frequently asked questions
Penetration testing, also known as ethical hacking or white-hat hacking, is a security assessment technique that involves simulating real-world cyberattacks on a system or network to identify vulnerabilities and assess the effectiveness of security measures. It helps organizations proactively uncover weaknesses and improve their security posture.
Penetration testing is crucial for identifying potential security vulnerabilities that malicious actors could exploit. It helps businesses understand their risk exposure, prioritize security investments, and implement appropriate measures to protect sensitive data, infrastructure, and applications.
The penetration testing process typically involves several stages, including reconnaissance, scanning, vulnerability identification, exploitation, and reporting. Ethical hackers attempt to exploit vulnerabilities in a controlled manner to assess the impact and provide actionable recommendations for remediation.
FluidOne offers comprehensive penetration testing services performed by skilled cybersecurity professionals. We follow industry best practices and employ advanced tools and techniques to identify vulnerabilities and assess their potential impact. Our detailed reports provide actionable insights and recommendations to improve your security defenses.
Take the first step to bolster your cyber security defenses with FluidOne's penetration testing as a service
Don't wait for a cyber-attack to happen. Our Penetration Testing as a Service solution empowers you to proactively identify vulnerabilities, strengthen your security defenses, and gain peace of mind. Start securing your business today!
"They are brilliant pen testers. This is the jewel in the crown of SC. The individuals are very good and the reporting is very consumable for me and my team."
"The value they give us is the key reason. This comes from the quality of their staff and their long term partnership with us, including their knowledge of what we need. Cost is less of an issue - we could find a cheaper vendor tomorrow (especially for basic pen testing) but we would lose out on SC's experience and relationship with us."
"I am very pleased with SC. They always do a good job, they're very thorough, their consultants are approachable and they take time to engage with our internal project teams. I'm really impressed with their work and they are still my go-to vendor."
Get a quote for our penetration testing services
Ready to enhance your cybersecurity defenses?
Our expert team is ready to help you enhance your cybersecurity defenses through
comprehensive penetration testing services tailored to your specific needs.
